Question
In: Computer Science
For the past several weeks you have addressed several different areas of telecommunications and information technology...
For the past several weeks you have addressed several different areas of telecommunications and information technology in relation to different types of communication across the organizational footprint of Sunshine Health Corporation. Review the work you have done and formulate the Network Security Plan to be implemented across the network footprint. This is not to be an overly detailed report but to address different network concerns and recommendations for improving and securing organizational data, personnel records, intellectual property, and customer records.
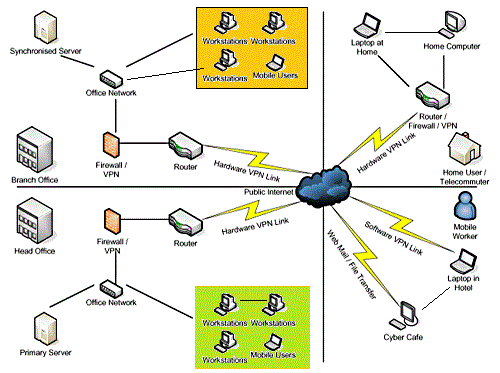
Please address the narrative plan as well as a network diagram (no IP addresses, or circuit data required) and what is being done to secure the network at different levels of the OSI model and the organizational structure. Please make sure that you bring in a minimum of two external sources to strengthen and support your presentation.
The assignment should be 5-6 pages of content not counting title page, reference page or appendices (diagrams, budget sheet, equipment list, etc.). Please follow APA format.
Solutions
Expert Solution
The Physical Layer
Exploiting the Physical Layer could suggest some
type
of physical action, like disrupting a power source,
changing of interface pins, or the
cutting of cables. Simply tampering with someone’s
fuse box outside their office can
cause a disruption of service. Faulty power is a
problem that can be caused accidentally
by the power company, or intentionally by your
competitor tampering with the fuse box.
By installing an Uninterrupted Power Supply (UPS) to
your system you can avoid many
unrecoverable power associated problems. Add an UPS to
your critical system and when
power is interrupted your UPS will give you time to
perform an orderly shutdown. This is
important because abrupt termination of power to any
electrical equipment has potential
for damage. With regards to your competitor tampering
with your fuse box, a lock may
deter them.
A less obvious physical component of networking is
Wireless Ethernet. IEEE
802.11 (IEEE standards can be found at
http://www.ieee.org) explains the standards for
Wireless Ethernet. Replacing wire with radio waves
transporting electrical impulses
wireless technologies use frequencies and Wireless
Ethernet uses 2.4 GHz (Giga Hertz).5
If binary is transmitted over a 2.4GHz band, and
a
leaky microwave oven is also sending 2.4GHz patterns,
it is not hard to guess that there is
a chance of signal disruption. Any old leaky ovens can
cause real wireless problems, and
in the worst case scenario – a Denial of Service
The Data Link Layer
RFC 826 first discussed a protocol called ARP.8
ARP stands for Address
Resolutions Protocol. Now that isn’t going to mean a
lot until you think, “What is it that
we are trying to address?” Network Interface Cards
(NIC) exist to give computers the
ability to talk to each other. To do this they need to
be able to find each other. In order to
do this they are assigned a single unique address –
known as a MAC Address. Media
Access Control (MAC) Addresses are used by ARP. ARP is
a protocol that allows a
source computer to ask other computers if they know
the MAC address of the machine it
wants to speak with. Hopefully the destination machine
will reply, and say something
along the lines of “I know who you are after – that’s
me!” Of course if no one knows who
the source is asking after then the information is
sent to a device like a router.
So now
we see that computers talk to each other, and they use
NICs to do this and the way the
NICs can find each other is via ARP.
The Network Layer
The most important part of understanding Layer 3 –
Network Layer principles is
knowing that routers make decisions based on Layer 3
information. Routers are machines
that decide how to send information from one logical
network to another. Routers
understand the Internet Protocol (IP) and base routing
decisions on that information.
So from the information you have so far we should be
able to determine a process.
ARP matches a MAC Address to an IP address, and
Routers make forwarding decisions
based on IP addresses. If an attacker wants to cause
problems when they are physically
located within the network then they can ARP cache
poison, but what if they are outside
of the network? They can use routers.
The Transport Layer
One way the Transport Layer ensures that there is
reliability and error checking is
through the Transport Control Protocol (TCP). You may
have heard of TCP/IP, this is the
TCP protocol working over the Internet Protocol (IP).
Another protocol used at Layer 4
is UDP (User Datagram Protocol). TCP and UDP are
individually described as:
TCP, written in 1980 within RFC 761 by Information
Sciences Institute
University of Southern California. TCP was originally
produced for the
United States Department of Defence. The original
document found in the
reference above describes TCP as: “The Transmission
Control Protocol
(TCP) is intended for use as a highly reliable
host-to-host protocol
between hosts in packet-switched computer
communication networks, and
especially in interconnected systems of such
networks.” Highly reliable
host-to-host communications would be file transfers,
where loss of data
would be unacceptable.
“UDP (User Datagram Protocol) is a communications
protocol that offers
a limited amount of service when messages are
exchanged between
computers in a network that uses the Internet
Protocol).” The type of
information that can be transmitted using UDP where
reliability is not as
important as file transfers would be video streaming.
If a single packet
was lost during a video streaming session then that
packet probably would
not be critical to the stream. In this case accuracy
is traded for speed.
Inventory Your Current Security
Technologies
Do you have any of the following?
• Firewall, to keep unauthorized users off your network
• Virtual private network (VPN), to give employees, customers, and
partners secure access to your
network
• Intrusion prevention, to detect and stop threats before they harm
your network
• Content security, to protect your network from viruses, spam,
spyware, and other attacks
• Secure wireless network, to provide safe network access to
visitors and employees on the go
• Identity management, to give you control over who and what can
access the network
• Compliance validation, to make sure that any device accessing the
network meets your security
requirements
Identify Your Most Important Digital Assets and Who Uses Them
• Exactly what are your company's digital assets (such as
intellectual property and customer
records)?
• What are they worth?
• Where do those assets reside?
• Who has access to these assets, and why? Can all employees access
the same assets?
• Do you extend access to business partners and customers?
• How do you control that access?
What Would a Security Breach Do to Your Business?
• What is the potential financial impact of a network outage due to
a security breach?
• Could a security breach disrupt your supply chain?
• What would happen if your Website went down?
• Do you have e-commerce features on your site? How long could the
site be down before you lost
money?
• Are you insured against Internet attacks, or against the misuse
of your customers' data? Is this
insurance adequate?
• Do you have backup and recovery capabilities to restore
information if necessary after a security
breach?
Consider Your Current and Future Needs
• How do you expect your business plan to evolve over the next few
years?
• How recently have you updated your network equipment? Software?
Virus definitions?
• What type of security training do you provide to your
employees?
• How will growth affect your digital assets and their value to
your business as a whole?
• In the future, are you likely to have a greater need for remote
employees, customers, or partners
to access those digital assets?
Related Solutions
Several of our readings in past weeks have been on the effects on health of a...
You have been working with the arrays for the past few weeks and you have learned...
How is Access and use of technology resources addressed in an organization? Do you have any...
Over the past seven weeks, we have explored different decades of US history and applied principles...
Over the past seven weeks, we have explored different decades of US history and applied principles...
Stock market is going crazy over the past several weeks and one of the discussions has...
You have spent the past four weeks away from work serving as a juror in a...
Information Technology (IT) is an application of computers and telecommunications which stores, retrieves, transmits and manipulates...
You are a middle level manager and during the last few weeks you have experienced several...
During the past weeks, you have been introduced to software development planning techniques and tools. You...
- 1. The activation energy of a certain reaction is 41.5kJ/mol . At 20 ?C , the...
- Give TWO pieces of evidence that you've successfully made methyl salicylate. Remember when you cite TLC...
- Describe briefly the evolution of Craniata and Vertebrata.
- How many grams are in a 0.10 mol sample of ethyl alcohol?
- For this assignment you will write a program with multiple functions that will generate and save...
- How many grays is this?Part A A dose of 4.7 Sv of γ rays in a...
- how to operate a business?
 venereology answered 3 months ago
venereology answered 3 months ago