Question
In: Computer Science
A consultant has recommended your organization look to increase its security profile in relation to SMTP...
A consultant has recommended your organization look to increase its security profile in relation
to SMTP traffic. Management has asked you devise a firewall-specific strategy to address the
recommendation. What strategy would you recommend, and why?
Your answer should be approximately 200-250 words in length.
Solutions
Expert Solution
Solution:
- SSL Inspection decrypts SSL-encrypted SMTP connections. For incoming connections, your mail server's SSL certificates are used.
-
The DNS blacklist database is queried via a DNS lookup using the sender's IP address. If the DNS reputation database is not available, the email is not modified. If the domain or IP address is blacklisted, the email's subject line is modified to start with
[SPAM]and the following non-configurable MIME type headers are set:-
X-Spam-Prev-Subject:Your email subject without the [SPAM] tag. -
X-Spam-Flag: YES -
X-Spam-Status: Yes -
X-Spam-Level: ***
-
- Email attachments are scanned by the virus scanner. If malware is found, the attachment is stripped from the email and replaced by a customizable text informing the user that the malicious attachment has been removed
Some of the steps to be taken are,
Step1. Import the mail server certificates
import the SSL certificates of your internal mail server(s). For more information, see How to Use and Manage Certificates with the Certificate Manager.
Step 2: Enable virus protection for mail traffic
-
Enable virus scanning and SSL Inspection in the firewall.
- Go to FIREWALL > Settings.
- In the Firewall Policy Settings section, enable TCP Streams Reassembly.
- Make sure that Application Control is enabled.
- In the Virus Protection section,
- Set Enable Virus Protection to yes
- (Optional) Enable Advanced Threat Detection. For more information, see Advanced Threat Protection (ATP/ATD).
- In the Mail Security section, enter the public IP address that your mail server domain's MX record resolves to in the Mail Server SSL Certificates section, select the mail server SSL certificate from the Certificate list, and click +.
- Enter the FQDN of the DNS Blacklist Server.
Default:
b.barracudacentral.org
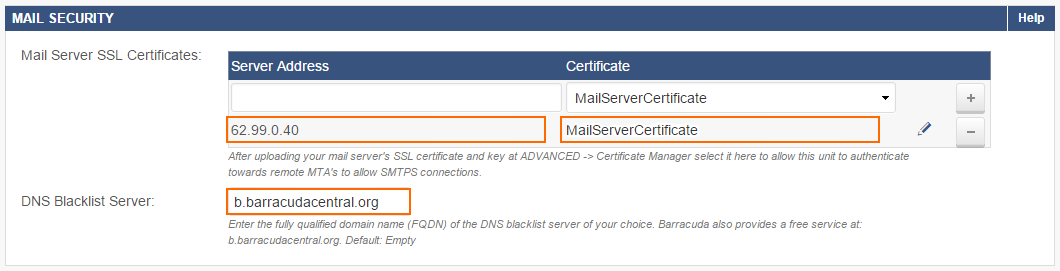
- Click Save.
Step 3. Create a DNAT access rule for incoming SMTP traffic
Enable Application Control, SSL Interception, and Virus Protection in the access rule.
- Go to FIREWALL > Firewall Rules.
- Create an access rule with the following settings:
- Action – Select DNAT.
- Connection – Select No SNAT.
- Source – Select Internet, and click +.
- Network Services – Select SMTP, and click +.
- Destination – Enter the public IP address that your mail server domain's MX record resolves to, and click +.
- Redirect – Enter the IP address(es), or select a network object for your internal mail server(s), and click +.
- Enable Application Control, SSL Inspection, Virus Protection,
and Mail Blacklist Checks.
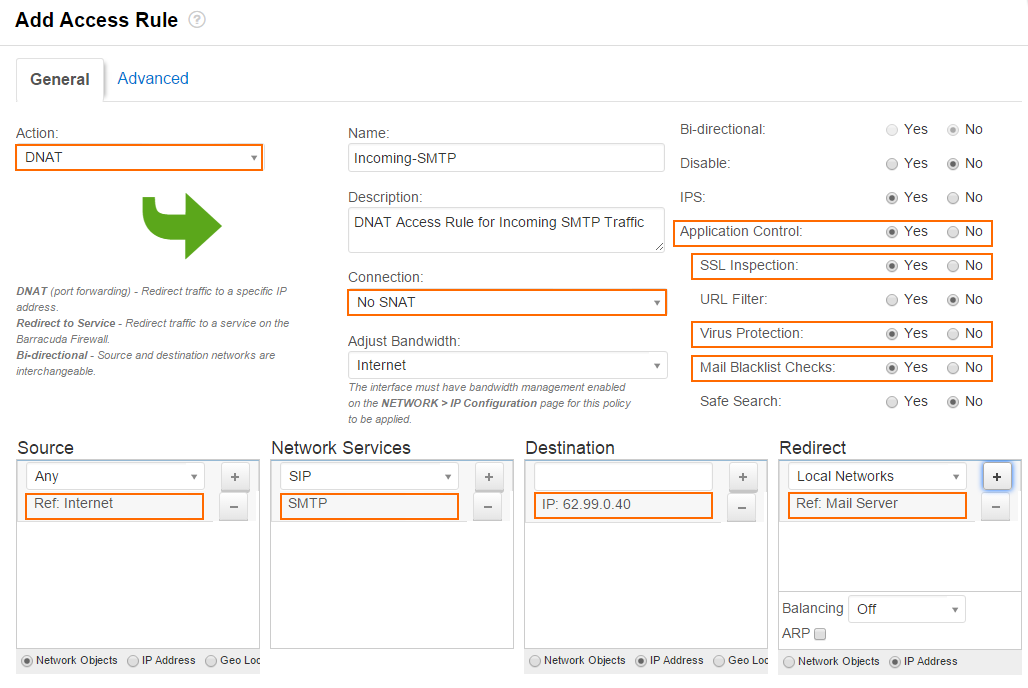
- Click Save.
Related Solutions
A consultant has recommended your organization look to increase its security profile in relation to SMTP...
A consultant has recommended your organization look to increase its security profile in relation to SMTP...
A consultant has recommended your organization look to increase its security profile in relation to SMTP...
A security consultant has observed that the attempts to breach the security of the companys computer...
A security consultant has observed that the attempts to breach the security of the companys computer...
As you increase the security of your network, you are concerned that the added security measures...
Your nonprofit organization wishes to increase the efficiency of its fundraising efforts. What sort of data...
List the capability(ies) profile needed for a typical business position in an organization of your choice.
Explain what a functional organization is in relation to a horizontal organizational structure and provide its...
Discuss the potential security challenge in your life or your organization, despite that the highlight of...
- Project 7-6: Sales Tax Calculator Create a program that uses a separate module to calculate sales...
- On June 30, Sharper Corporation’s stockholders' equity section of its balance sheet appears as follows before...
- In this journal you are asked to take the role of a mayor or congressional representative...
- Answer correctly the below 25 multiple questions on Software Development Security. Please I will appreciate the...
- 1. The activation energy of a certain reaction is 41.5kJ/mol . At 20 ?C , the...
- Give TWO pieces of evidence that you've successfully made methyl salicylate. Remember when you cite TLC...
- Describe briefly the evolution of Craniata and Vertebrata.
 venereology answered 1 year ago
venereology answered 1 year ago