Question
In: Computer Science
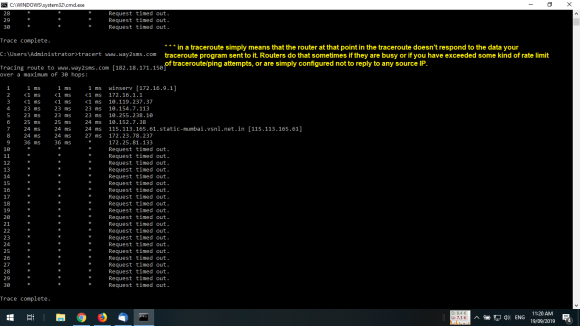
If you can run “traceroute/tracert” between machines in your organization. List three concrete applications to use...
- If you can run “traceroute/tracert” between machines in your organization. List three concrete applications to use trace route for cybersecurity?
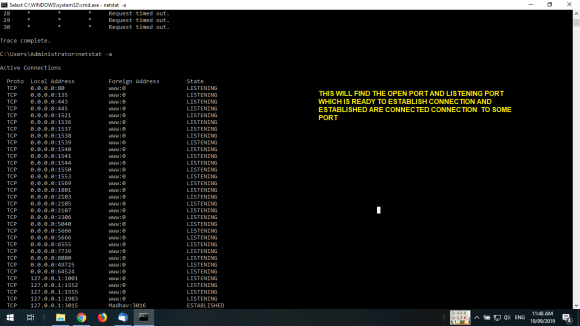
- How to use ”netstate/netstat” to discover malicious activities in your machine?
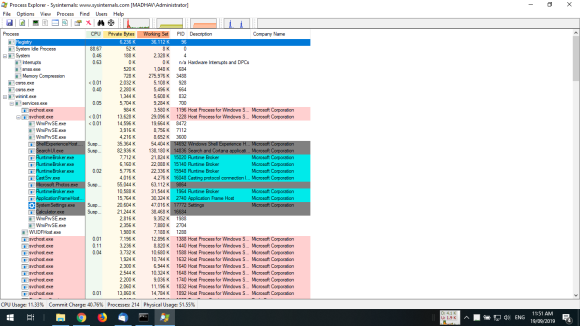
- Install and use Process Monitor “Procmon” (you can download from https://docs.microsoft.com/en-us/sysinternals/ (Links to an external site.)) and then show how to list all running processes that run “RegCreateKey” operation with unsuccessful results.
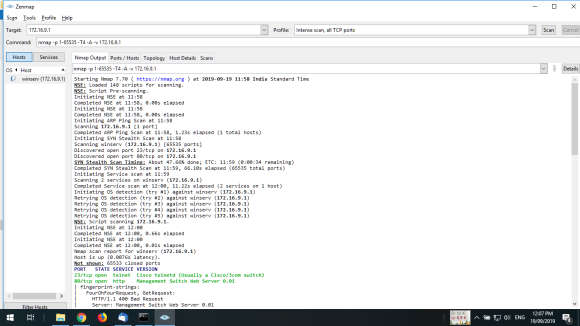
- Show how to use Nmap to do IP scanning using TCP and ICMP and port scanning using Stealth FIN. Show the command and the output.
Solutions
Expert Solution
Answer 1
***********
Answer 2
***********
Answer 3
***********
Answer 4
***********
if you have any doubt then please ask me without any hesitation in the comment section below , if you like my answer then please thumbs up for the answer , before giving thumbs down please discuss the question it may possible that we may understand the question different way and we can edit and change the answers if you argue, thanks :)
Related Solutions
1. If you can run “traceroute/tracert” between machines in your organization.List three concrete applications to use...
1. If you can run “traceroute/tracert” between machines in your
organization.List three concrete applications to use trace route
for cybersecurity?
2.How to use” netstate/netstat” to discover malicious activities
in your machine?
3. use Process Monitor “Procmon” show how to list all running
processes that run “RegCreateKey” operation with unsuccessful
results.
4.Show how to use Nmap to do IP scanning using TCP and ICMP and
port scanning using Stealth FIN. Show the command and the
output.
List three applications that use UDP and three applications that use TCP and explain why those...
List three applications that use UDP and three applications that
use TCP and explain why those applications use the selected
Transport layer protocol.
What are three specific and concrete ways you can immediately use to commit to developing greater...
What are three specific and concrete ways you can immediately
use to commit to developing greater intention within your current
organization? You can include your current professional
organization, or if you do not currently have one, consider a
college organization you belong to, or consider your family
Briefly describe 3 types of transition stragegies an organization can use to run both IPv4 and...
Briefly describe 3 types of transition stragegies an
organization can use to run both IPv4 and IPv6
concurrently.
List and describe five benefits and three costs that an organization can expect when implementing an...
List and describe five benefits and three costs that an
organization can expect when implementing an EMS that conforms to
the ISO 14001:2015 requirements. What barriers might prevent the
organization from realizing these benefits? How can these costs be
minimized?
A manufacturer has three machines A, B, and C. Machines A and B can be operated...
A manufacturer has three machines A, B, and C. Machines A and B
can be operated for at most 12 hours whereas machine C must be
operated for at least 5 hours a day. These three machines produce
only two items X and Y. Product X requires 1 hour from machine A,
two hours from machine B and 1 hour from machine C. Product Y
requires 2 hours from machine A, one hour from machine B and 1.25
hours from...
What are some lean applications you can use in a medical facility? Explain…
What are some lean applications you can use in a medical
facility? Explain…
Choose two applications from the list below. You should make your selections so that you are...
Choose two applications from the list below. You should make
your selections so that you are able to describe both points of
similarity and points of difference when answering the questions
that follow.
• Electronic file transfer
• Electronic mail
• Bit-torrent
• Internet Relay Chat (IRC)
• The Domain Name System (DNS)
• IP Telephony (VoIP, not Skype or Facetime, etc.)
• Real-time streaming (Not web-based solutions such as Youtube,
Facebook, Instagram, etc.)
Answer the following questions about both...
a) List some applications which find batch-mode processing useful. Justify your answer. b) List some applications...
a) List some applications which find batch-mode processing
useful. Justify your answer.
b) List some applications which find interactive-mode processing
useful. Justify your answer
A factory has three machines capable of producing widgets. All three machines together can produce 191...
A factory has three machines capable of producing widgets. All
three machines together can produce 191 widgets per hour. Machine A
and machine B together can produce 129 widgets per hour, while
machine A and machine C can together produce 137 widgets per hour.
How many widgets per hour can each machine produce?
A factory has three machines capable of producing widgets. All
three machines together can produce 242 widgets per hour. Machine A
and machine B together can produce...
ADVERTISEMENT
ADVERTISEMENT
Latest Questions
- A bicycle wheel has a diameter of 63.9 cm and a mass of 1.86 kg. Assume...
- Cane Company manufactures two products called Alpha and Beta that sell for $150 and $110, respectively....
- What’s the cost of each component of capital and which need to be adjusted? What do...
- Answer the following questions 1) How does ASC 606 — Revenue From Contracts With Customers(new standard...
- Project 7-6: Sales Tax Calculator Create a program that uses a separate module to calculate sales...
- On June 30, Sharper Corporation’s stockholders' equity section of its balance sheet appears as follows before...
- In this journal you are asked to take the role of a mayor or congressional representative...
ADVERTISEMENT
 venereology answered 1 year ago
venereology answered 1 year ago