Question
In: Computer Science
Suppose your RSA public-key factors are p = 6323 and q = 2833, and the public exponent e is...
Suppose your RSA public-key factors are p = 6323 and q = 2833, and the public exponent e is 31. Suppose you were sent the Ciphertext 6627708. Write a program that takes the above parameters as input and implements the RSA Decryption function to recover the plaintext. Use C or C++ programming language.
Solutions
Expert Solution
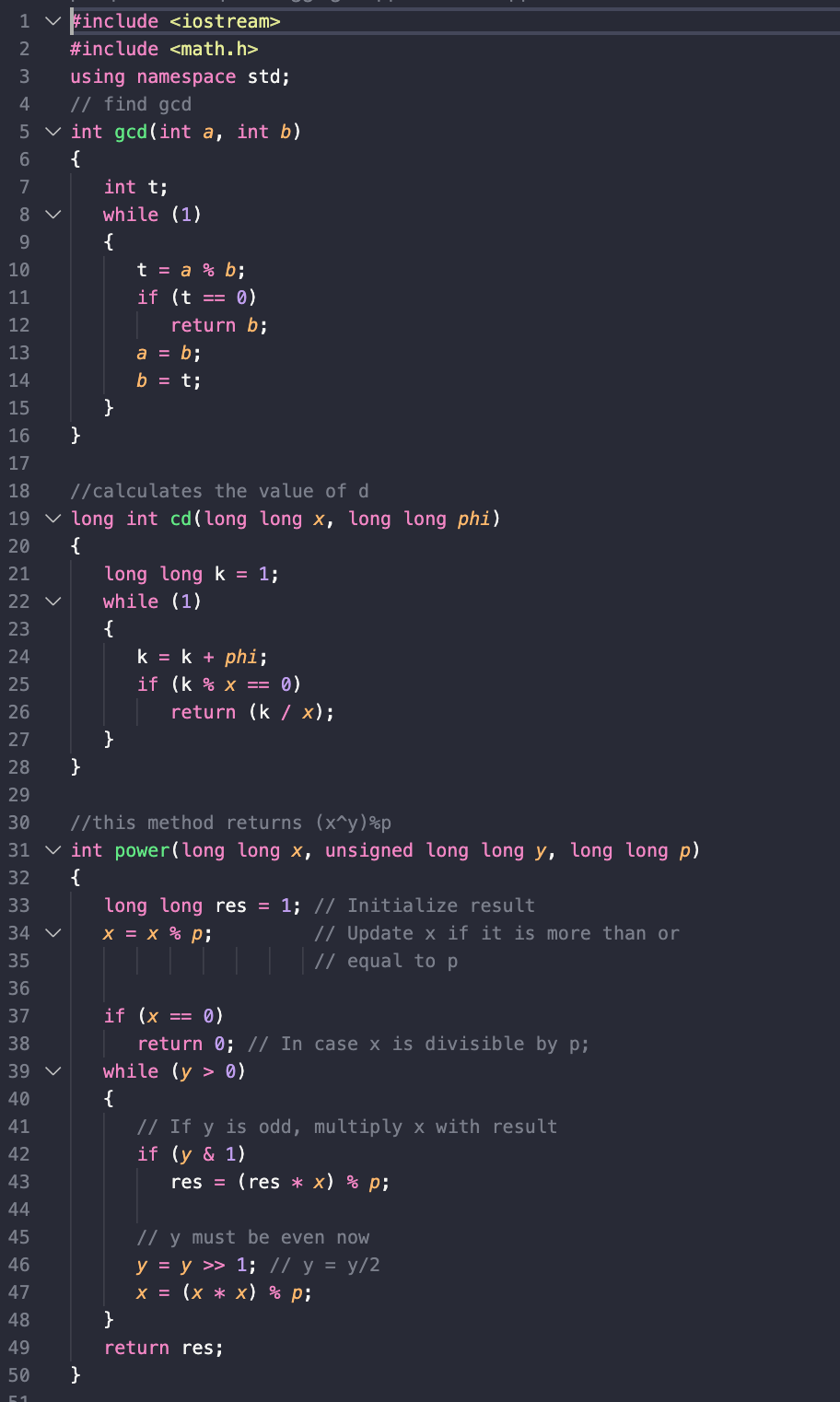
#include <iostream>
#include <math.h>
using namespace std;
// find gcd
int gcd(int a, int b)
{
int t;
while (1)
{
t = a % b;
if (t == 0)
return b;
a = b;
b = t;
}
}
//calculates the value of d
long int cd(long long x,long long phi)
{
long long k = 1;
while (1)
{
k = k + phi;
if (k % x == 0)
return (k / x);
}
}
//this method returns (x^y)%p
int power(long long x, unsigned long long y, long long p)
{
long long res = 1; // Initialize result
x = x % p; // Update x if it is more than or
// equal to p
if (x == 0) return 0; // In case x is divisible by p;
while (y > 0)
{
// If y is odd, multiply x with result
if (y & 1)
res = (res*x) % p;
// y must be even now
y = y>>1; // y = y/2
x = (x*x) % p;
}
return res;
}
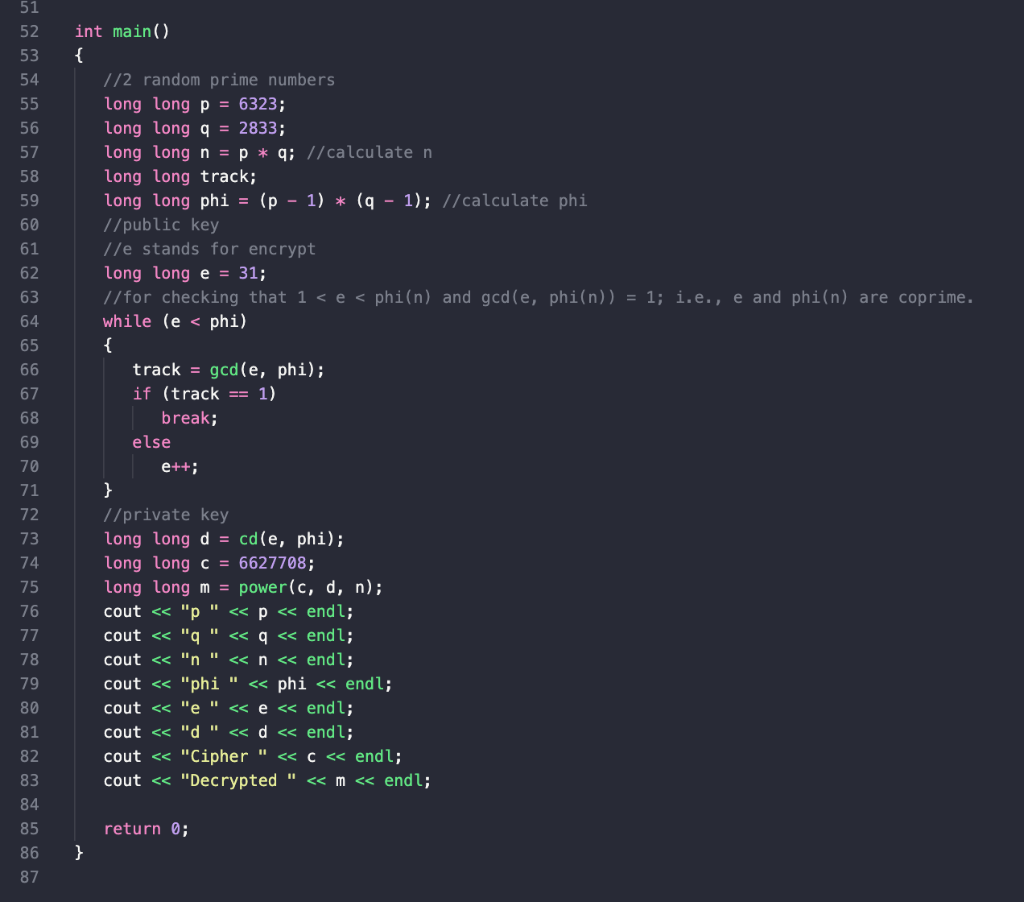
int main()
{
//2 random prime numbers
long long p = 6323;
long long q = 2833;
long long n = p * q; //calculate n
long long track;
long long phi = (p - 1) * (q - 1); //calculate phi
//public key
//e stands for encrypt
long long e = 31;
//for checking that 1 < e < phi(n) and gcd(e, phi(n)) = 1; i.e., e and phi(n) are coprime.
while (e < phi)
{
track = gcd(e, phi);
if (track == 1)
break;
else
e++;
}
//private key
long long d = cd(e,phi);
long long c = 6627708;
long long m = power(c,d,n);
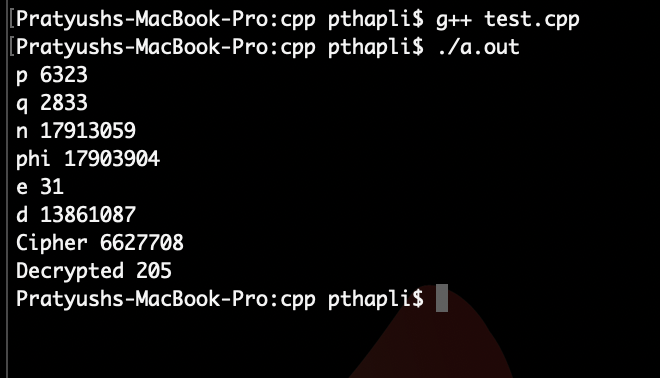
cout<<"p "<<p<<endl;
cout<<"q "<<q<<endl;
cout<<"n "<<n<<endl;
cout<<"phi "<<phi<<endl;
cout<<"e "<<e<<endl;
cout<<"d "<<d<<endl;
cout<<"Cipher "<<c<<endl;
cout<<"Decrypted "<<m<<endl;
return 0;
}
Related Solutions
Given the prime factors p and q, the encryption exponent e, and the ciphertext C, apply...
In the RSA cryptosystem, Alice’s public key (N, e) is available to everyone. Suppose that her...
In the RSA public-key encryption scheme, each user has a public key, e, and a private...
a) In a public-key system using RSA, n=77 and its public key is e=23. What is...
Consider an RSA system with p = 7109 and q = 7919. Generate a public and...
Write C program for RSA encryption and decryptin, where: p = 11,q = 5, e =...
Please perform encryption and decryption given the following values of an RSA public key cryptosystem; p=17,...
Exercise 9.9.1: Breaking RSA by factoring. Bob publishes his public key (e, N) = (109, 221)...
RSA: Alice wishes to send Bob the message POET. Suppose Bob chooses P = 29, Q...
it is a question of discrete math RSA is the most widely used public key cryptosystem....
- Redox/Oxidation lab with Metals and Halogens So basically we were testing different reactions and observing changes....
- CORAL LANGUAGE ONLY Write a function DrivingCost with parameters drivenMiles, milesPerGallon, and dollarsPerGallon, that returns the...
- do you believe, as bonilla-silva does, that convert forms of racism are widespread? why or why...
- A bicycle wheel has a diameter of 63.9 cm and a mass of 1.86 kg. Assume...
- Cane Company manufactures two products called Alpha and Beta that sell for $150 and $110, respectively....
- What’s the cost of each component of capital and which need to be adjusted? What do...
- Answer the following questions 1) How does ASC 606 — Revenue From Contracts With Customers(new standard...
 venereology answered 1 month ago
venereology answered 1 month ago